I’m selling my Evo. Here are more pictures.
Continue reading ‘2008 Mitsubishi Evo photos’Weird Al Yankovic sings “The Elements”
Published May 20th, 2018 in General and Recordings. 0 CommentsMy wife and I got to see “Weird Al” Yankovic in concert in Monterey last Thursday night. He covered Tom Lehrer’s “The Elements”. This is interesting because….
- Al doesn’t often do covers, but often does parodies.
- Tom’s song was itself a parody.
- The source material (from “The Pirates of Penzance”) was, some say, partly a response to the rampant musical piracy in the U.S. at the time.
So there’s a thing. Anyway, I really enjoyed the concert, and I wanted to test some experimental binaural microphones I’d constructed. Bada-bing! Bada-boom!
So, please Don’t Download this Song, and if you want to help Al and Tom get their Solid Gold Humvees, then support them by doing stuff!
The Elements
Oh, and Emo Philips is a great opener, very funny, and (despite rumor) still alive.
Yes, it’s done! Relive the excitement and adventure of cramming a full cast and orchestra into a band room!
Usual caveats about “this was not a studio recording”, etc.
Continue reading ‘Princess Ida Sitzprobe recordings’
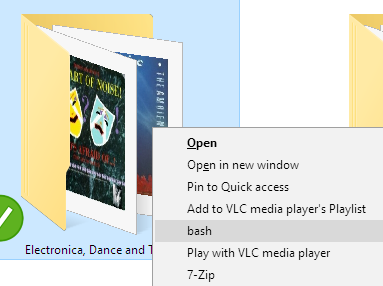
Cygwin bash in the context menu
Published December 21st, 2016 in Computer nitpicks and General. 0 CommentsGetting the Cygwin bash (mintty) in the Windows context menu is a little esoteric. Mostly this is because you have to set the directory at Windows time, rather than Cygwin time. (Otherwise you would have to convert the directory pathname with drives and colons into Posix-ish format of /cygdrive/D/….)
Here’s the way that works for me. Add the Windows Registry key
HKEY_CLASSES_ROOT\Directory\shell\bash\command
and set the default string (REG_SZ) to the impressively unwieldy value of
C:\utils\cygwin\bin\mintty.exe -i /Cygwin-Terminal.ico --dir "%V" /bin/env CHERE_INVOKING=1 /bin/bash -l
(Modify the mintty pathname as required. Also, –dir is only supported on newer versions of mintty.)